Executive Summary
Mobile Driver’s Licenses (mDLs) are emerging as a secure, state-issued digital identity credential, with adoption spreading across more than a dozen states. While some customers may view mDLs as an alternative to Credential Service Providers (CSPs), there are differences in capabilities that make mDLs and CSPs an “and,” not an “or.”
As it stands today, mDLs are helpful for presentation of demographic information in association with point of sale, retail, and other “attended” transactions. However, there has been limited adoption for online transactions because of:
- Delays releasing the ISO 18013-7 standards that govern online, unattended transactions
- Limited attributes in the payloads (e.g., SSN needed for many online transactions, but mDLs don’t have them)
- Poor online authentication experiences using native wallets and mDL apps
- Lack of audit logging and telemetry data from device-side digital wallets mean limited ability to protect high risk transactions (i.e., no informed analytics, fraud detection, or continuous monitoring)
A complementary model is one where mDLs serve as modern, high-assurance identity evidence that can be paired with the attribute validation, resolution, fraud prevention, life cycle management, and authentication capabilities of a CSP. This “and” model will result in the most secure and frictionless transactions across the widest range of use cases.
ID.me’s Video Chat Pathway offers a secure alternative to self-service for users without a presence in authoritative records. This verification pathway has helped 10.1 million users verify their identity and access critical services, closing approximately 75% of the digital divide created by credit bureaus and data brokers.
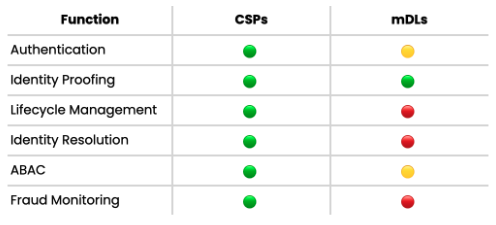
mDLs can strengthen the security of an identity verified by CSPs, and CSPs and digital wallets can increase the utility of mDLs. If a CSP issues a credential using an mDL, it can then pair it with other attributes that an mDL doesn’t have natively, such as SSN, professional certifications, address history, phone numbers, and email addresses. Combining the mDL with additional attributes and packaging them into a server-side digital wallet enables secure authentication across any website that uses open protocols, increases portability of the credentials (i.e. acceptance at more places online), and increases the layers of fraud controls that prevent abuse of the mDL.
This article dives deeper into how mDLs and CSPs will work together to increase security and reduce friction in our increasingly digital – and increasingly vulnerable – economy.
Situation / Background
What are mDocs and mDLs?
Mobile Documents (mDocs) are digital versions of government-issued credentials (driver’s licenses, identity cards, etc.) intended to be securely stored and presented from a user’s mobile device. A leading example is the mobile Driver’s License (mDL) – the digital equivalent of a physical driver’s license.
With the introduction of AI, fake identity documents have become increasingly difficult to detect. Physical security features like holograms, watermarks, etc. are becoming easier to fabricate in an online setting with emerging technologies. Unlike a static image or PDF, an mDL offers cryptographic proofs (e.g., signed claims, device binding) such that a relying party (RP) can verify that the credential was issued by a legitimate authority and has not been tampered with digitally. This provides the RP with additional confidence that the digital evidence submitted is legitimate.
Rollout and Adoption
- There is high intent to use mDLs.
- A newly published ISO standard (ISO/IEC 18013-7) now formally defines the use of mDLs for online identity proofing (Biometric Update).
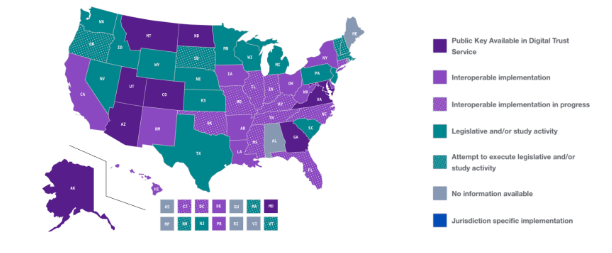
- Today, 19 states have achieved some level of mDL deployment (AAMVA Jurisdiction Map).
- More broadly, up to 26 states are actively taking steps (pilots, planning, or implementation) toward mDL deployment (Biometric Update).
- However, adoption is currently low.
- According to a Government Technology survey, many states’ adoption rates remain in the single-digit percentages (GovTech).
- Arizona is the only state that has >10% of their residents who have adopted an mDL (mDL Connection).
- Differences remain in mDL implementations for web presentation: California is the only state that currently conforms with ISO 18013-7 for web or mobile app acceptance of mDLs (mDL Connection).
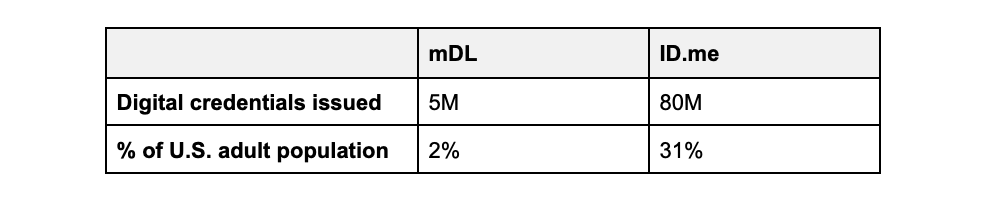
- As of recent counts, 5 million+ mDLs have been issued across the U.S. (Government Technology).
- The slow pace of adoption is attributed to technical, privacy, legal, and ecosystem challenges (Biometric Update).
- According to a Government Technology survey, many states’ adoption rates remain in the single-digit percentages (GovTech).
Despite growing momentum, mDLs remain a developing technology: they are not yet universally accepted, and usage is uneven across states and contexts. The overwhelming majority of mDL use cases are related to in-person presentation rather than remote/online presentation.
Misperception that mDLs are a substitute for CSPs
As mDLs emerge as a more modern form of identity evidence, some organizations are exploring the notion of using mDLs instead of – or as a replacement for – CSPs for authentication and verification.
However, adopting mDLs in a siloed or standalone manner – without CSP integration – leads to:
- Fragmented implementations that undermine foundational consistency needed for effective digital identity management
- Limited interoperability caused by partial adoption, utility, and lifecycle management
- Decreased security due to a lack of cross-communicating fraud signals, telemetry data, and audit logging
The challenge now is to define what “right” looks like: a model in which mDLs and CSPs coexist and reinforce one another.
Solution: Complementary use of mDLs and CSPs
A complementary model takes advantage of the strengths of both mDLs and CSPs, where mDLs strengthen the verification evidence for CSPs and CSPs increase the utility and security of mDLs for RPs.
- mDLs function as “SUPERIOR” identity evidence (a trusted, cryptographically verifiable credential) used during verification.
- The CSP ingests or verifies mDL-provided claims during initial identity proofing to streamline the verification experience.
- For CSPs that offer it, the mDL can be stored in a device-agnostic digital wallet.
- CSPs are responsible for managing the account lifecycle, including account registration, authentication, ongoing access, identity proofing, fraud detection, and support.
- The CSP can leverage the mDL during major lifecycle events (e.g., account recovery) to streamline the experience.
- CSPs continue to manage the account and additional identity signals, risk scoring, binding to other user attributes, and cross-domain interoperability.
In effect, the CSP acts as the orchestration layer, the central “hub,” while mDLs serve as one of several high-assurance forms of identity evidence. ID.me is targeting to accept and support mDLs in H2 2026.
Rationale
Fragmented, Siloed Implementations. When agencies build independent, “homegrown” identity systems, the result is redundant costs, inconsistent user experiences, and fractured security. If each organization attempts to implement mDL validation and authentication independently (outside of a CSP), they will incur duplicative engineering, compliance, and fraud infrastructure burdens and reoccurring operational costs. Additionally, they may fall short in usability, introducing friction and reducing online access rates.
Limited Payload / Attribute Coverage. An mDL typically contains a subset of identity attributes (name, birthdate, address, license details). In many IAM systems, additional attributes (e.g., Social Security Number, email address, phone number, etc.) are required for Attribute Based Access Control (ABAC), identity resolution, and other functions. mDLs alone may not supply these, limiting their utility as a standalone identity source.
Restricted Reach / Universality. Offering mDL as a replacement may exclude large populations and force parallel fallback systems.
- Only a subset of U.S. states issue or plan to issue mDLs (estimated 18–26 states).
- Many citizens lack smartphones or advanced technical literacy, making exclusive reliance on mDLs inequitable.
Missed Preverified Network Gains. The number of enrolled mDL users (~5M) is ~2% of the U.S. adult population. In contrast, there are over 150M digital wallets in the ID.me network (~55% of the US adult population), almost 80M of which have verified their identity to federal standards (~30% of the US adult population). Verification is generally a one-time event, and it is paired with strong multifactor authentication (MFA) for continued secure access. If an organization were to replace a CSP with an mDL option, it would force the ~80M people who have a valid digital identity to redo the verification event, some of whom likely depend on the video chat or in-person pathways ID.me uniquely offers.
Lack of Lifecycle & Support Infrastructure. CSPs provide many additional capabilities such as account recovery, end user support, and fraud mitigation. In a standalone mDL model, users would have no unified point of contact for issues (e.g., their updated last name is not showing on the mDL).
Absence of a Holistic Fraud Framework. mDLs improve security at the credential level, but they should not be assumed to be inherently more secure than CSPs. CSPs offer robust fraud programs that include behavioral analytics, device reputations, cross-risk scoring, or orchestration of fraud signals across contexts. CSPs bring a network effect to fraud detection and prevention – pooling signals across integrations and RPs – which is superior to isolated fraud programs.
In Louisiana, the LA Wallet mDL was exploited in one of the first documented cases of mDL-enabled financial fraud: criminals used stolen PII to access a victim’s mDL and generate fraudulent documents, which were then used to open bank accounts across multiple institutions (Biometric Update).
Lack of Auditability for High-Risk Transactions. While native digital wallets and state-issued apps enable convenient, device-bound credential presentation, they lack a critical component for high-risk use cases: audit logging. These wallets do not maintain verifiable records of who performed an action, when it occurred, or how identity data was used. If they do, this is not communicated to the RP. This absence of audit history makes them unsuitable for transactions that require traceability and accountability – such as updating a bank account for a payout or modifying sensitive personal information. Without a centralized audit trail, organizations have no means to investigate disputes, enforce compliance, or demonstrate non-repudiation.
Weak Support for Authentication (MFA). mDLs are designed primarily as a form of identity evidence. They prove who you are at a point in time, but they are not well suited for ongoing authentication. If a RP tries to use an mDL for re-authentication, the user would need to re-share sensitive identity data every time, exposing more personal information and adding friction. By contrast, CSPs offer and manage multiple reusable authenticators (e.g., passkeys) that enable strong MFA without repeatedly disclosing sensitive data.
Conclusion
mDLs represent a valuable step forward in secure digital identity, and the recent ISO standard for online identity proofing will accelerate their adoption. But mDLs are not a standalone solution. Their limited adoption, partial data payloads, and lack of lifecycle and fraud management make them insufficient on their own.
The right approach is a complementary model: CSPs continue to manage registration, authentication, identity proofing, support, and fraud prevention, while mDLs serve as high-assurance evidence that strengthens verification. This integration delivers security, scalability, and user trust without repeating the pitfalls of fragmented, siloed identity systems. ID.me looks forward to becoming one of the largest consumers of mDLs as adoption increases and support for ISO 18013-7 becomes more widespread.




